Virtualization Security: Stay Ahead of the Threat Curve
- 03 May, 2024 - 03 May, 2024
- 03 May, 2024
- Cameroon, Bamenda
Event Description
Virtualization Security: Stay Ahead of the Threat Curve
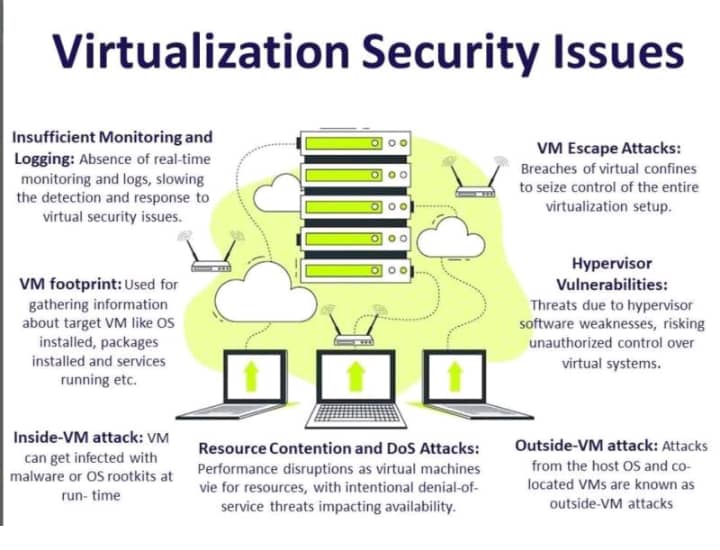
Virtualization security refers to the pratices, technologies, and strategies used to protect virtualized infrastructures, including virtual machines(VMs), hypervisors, and the underlying physical hardware. Virtualization, which allows multiple operating systems and applications to run on a single physical server, introduces unique security challenges compared to traditional environments.
Hypervisor Security: The hypervisor is the core component of virtualization that manages and allocates ressources to virtual machines. Securing the hypervisor is crucial as any compromise can affect all VMs running on the host. Techniques such as regular patching, minimizing the attack surface, and implementing access controls are essential.
Isolation: Ensuring Strong isolation between virtual machines is critical to prevent one compromised VM from affecting others. Techniques such as network segmentation, using separate VLANs or virtual switches for each VM, and deploying micro-segmentation solutions help enhance isolation.
VM Security: VMs themselves need to be secured like physical machines, including installing security updates, running antivirus software, and implementing access controls. Additionally, techniques like VM encryption can protect data at rest.
Virtual Network Security: Virtual networks within the virtualized environment need to be secured against attacks and unauthorized access. This includes implementing firewalls, intrusion detection and prevention systems (IDPS), and encryption for network traffic.
Management Plane Security: The Management interfaces and tools used to administer the virtualized environment must be secured to prevent unauthorized access or tampering. This envolves using strong authentication mechanisms, access controls, and encryption for management traffic.
Backup and Disaster Recovery: Implementing robust backup and disaster recovery solutions is crucial to mitigate the impact of security incidents or failures in the virtualized environment. Regular backups of VMs and critical data, along with testing of recovery procedures, are essential.
Monitoring and logging: Continuous monitoring of the virtualized environment, including logging of events and activities, helps detect and respond to security incidents promptly. Security information and event to centralize and analyze log data for signs of potential threats.