Zero Trust in Cybersecurity Awareness
- 30 Jan, 2024 - 30 Jan, 2024
- 30 Jan, 2024
- Cameroon, Bamenda

Event Description
🔐 Embrace Zero Trust: Strengthen Your Cybersecurity Armor! 🔐
Dear digital defenders, let's talk about an essential concept in today's cybersecurity landscape: Zero Trust. In a world where threats are constantly evolving, Zero Trust is a game-changing approach that can fortify your defenses and protect your digital assets. Here's what you need to know:
🔒 What is Zero Trust?
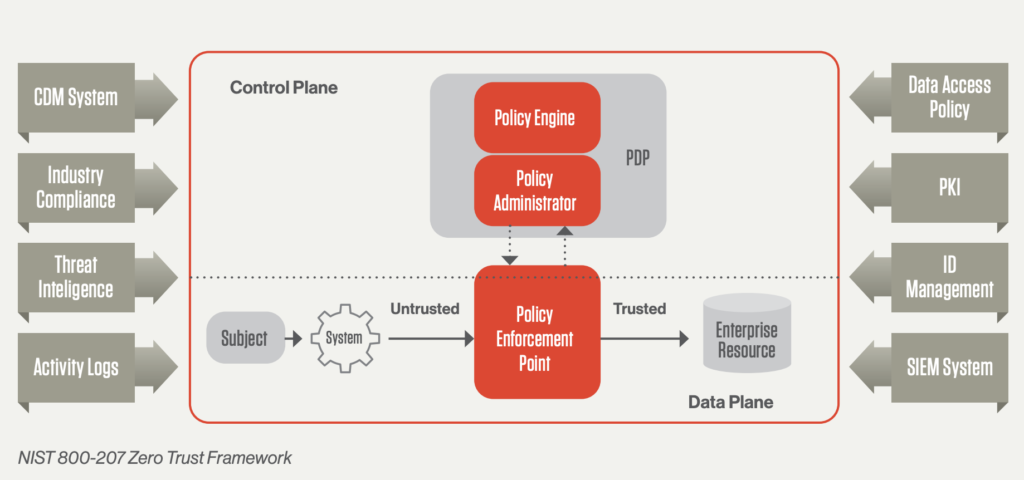
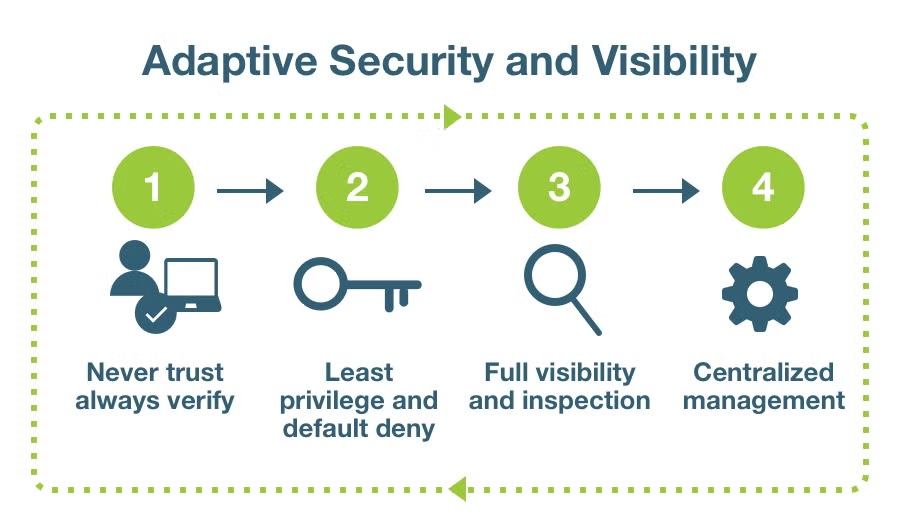
Zero Trust is a security model that challenges the traditional "trust but verify" approach. It operates on the principle of "never trust, always verify." In a Zero Trust environment, every user, device, and network component is treated as potentially untrusted, regardless of their location or previous credentials.
🔒 The Core Principles of Zero Trust:
1️⃣ Least Privilege: Grant users the minimal level of access necessary to perform their tasks. Limiting privileges reduces the potential impact of a security breach.
2️⃣ Continuous Authentication: Verify the identity and trustworthiness of users and devices at every interaction. Authentication should be ongoing, not just a one-time event.
3️⃣ Micro-Segmentation: Isolate and segment your network into smaller, more manageable zones. This way, even if one segment is compromised, the damage can be contained.
4️⃣ Strict Access Controls: Implement granular controls based on user context, device health, and other factors. Every access request should be evaluated and approved based on dynamic conditions.
🔒 Embracing Zero Trust Benefits:
✅ Enhanced Security: Zero Trust minimizes the risk of lateral movement within your network and limits the potential damage of a security incident.
✅ Improved Visibility: By continuously verifying and monitoring user and device activity, you gain a comprehensive view of your network's security posture.
✅ Agility and Scalability: Zero Trust allows for flexible access management, enabling secure remote work and accommodating dynamic business needs.
✅ Compliance and Data Protection: Zero Trust aligns with regulatory requirements and helps safeguard sensitive data, reducing the risk of data breaches.
🔒 Implementing Zero Trust:
Implementing Zero Trust is a journey, not an overnight transformation. Start by assessing your current security posture, identifying critical assets, and gradually implementing Zero Trust principles across your network.
Remember, Zero Trust is not a one-size-fits-all solution. Customize it to fit your organization's unique needs and seek guidance from cybersecurity professionals if needed.
Let's make Zero Trust the foundation of our cybersecurity strategy, creating resilient defenses against ever-evolving threats.