Simplified Cybersecurity Series: Top Firewall Use Case Firewall are essential for protecting networks and controlling access to services
- 06 May, 2024 - 06 May, 2024
- 06 May, 2024
- Cameroon, Bamenda
Event Description
Simplified Cybersecurity Series: Top Firewall Use Case
Firewall are essential for protecting networks and controlling access to services
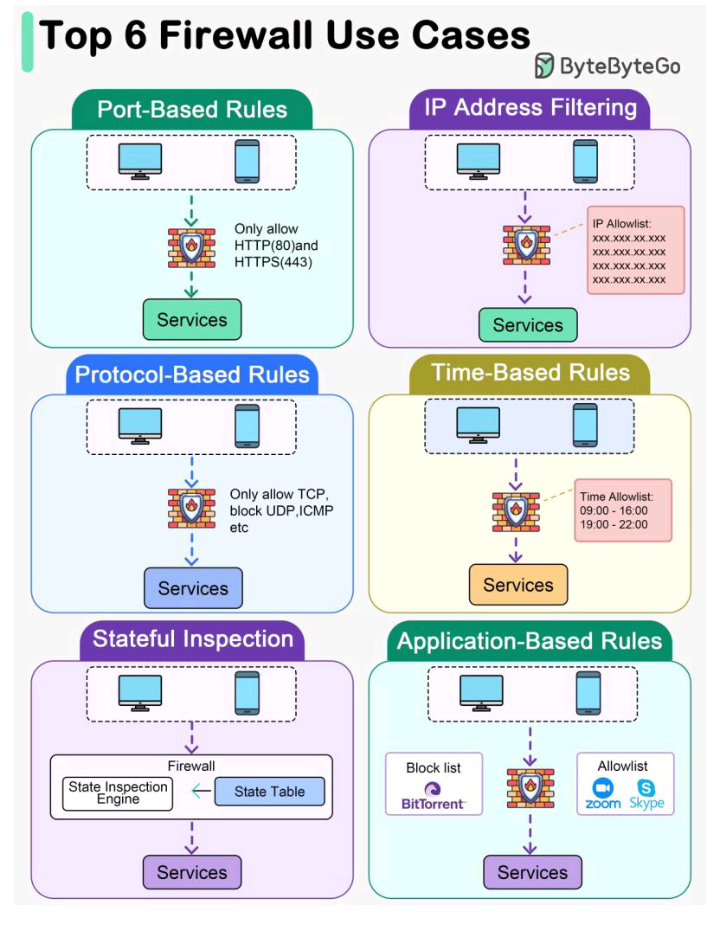
Port-based rules
-Port-based rules restrict traffic to specific ports
-These rules define which ports can be used to communicate with a particular service or application
-Networks administrators use them to limit the types of traffic that are allowed to enter or exit a network
-Port-based rules help prevent unauthorized access, data breaches, and others security threats.
IP address filtering
-IP address filtering is a securiting measure
-It allows access to services only from specific IP addresses
-Unauthorized IP addresses are denied access
-It helps prevent unauthorized access and protect the service from potential security threats.
Protocol-based rules
-Protocol-based rules are used in computer networking to restrict access to specific services based on the type of protocol being used.
-TCP is commonly used for reliable communication, while UDP is used for faster data ttransmission.
-ICMP is mainly used for diagnostic and error reporting purposes.
-Network administrators can control and limit access to network ressources based on the specific protocols being used.
Time-based rules
-Time-based rules allow for setting schedules for service access
-Access to certain services can be limited based on time
-Services can be made available only during specific hours
-These rules are helpful for managing and controlling access o services
Stateful inspection
-Stateful inspection is a firewall technology
-It exemines the state of network connections in a stable table
-It keeps track of all the connections passing through the firewall
-It makes intelligent traffic filtering decisions based on the state of these connections
-It can identify and block suspicious traffic that may otherwise pass through traditional firewalls.
Applications Based rules
-Firewalls have a feature called application-based rules.
-Application-based rules allow you to control traffic based on specific applications.
-you can allow or block traffic for applications such as BitTorrent, Zoom, and Skype.
-This feature gives you greater control over the traffic yhat passes through your network.
-It helps to ensure that your system is secure and running smoothly