Simplified Cybersecurity Series: How to we design a secure system?
- 08 May, 2024 - 08 May, 2024
- 08 May, 2024
- Cameroon, Bamenda
Event Description
Simplified Cybersecurity Series: How to we design a secure system?
Designing secure systems is important for a multitude of reasons, spanning from protecting sensentive information to ensuring the stability
and reliability of the infrastructure. As developers, we should design and implement the security guidelines by default.
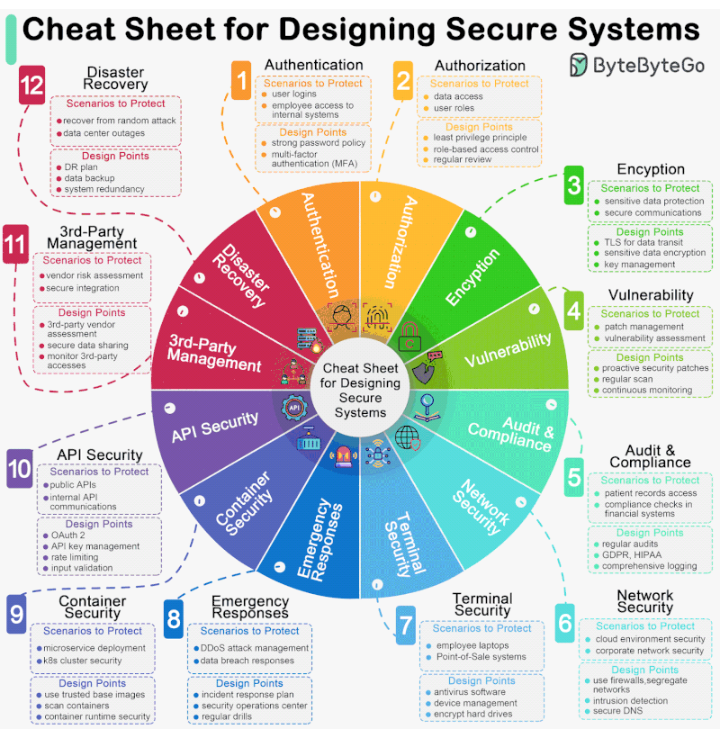
The diagram below is a pragmatic cheat with the use cases and key design points.
* Authentication - ensuring that the user or system is who they claim to be
* Authorization - granting appropriate access to the authenticated user or system, bassed on their role or privileges
* Encryption - securing data and communication channels through encryption techniques
* Vulnerability - identififying and fixing weaknesses in the system that could be exploited by malicious actors
* Audit & Compliance - monitoring and reporting system activity to ensure adherence to security policies and regulations
* Network Security - Protecting the system from unauthorized access or attacks through network security measures
* Terminal Security ensuring that physical and remote access points to the system are secure
* Emergency Responses - having procedures in place to respond to security incidents or emergencies
* Container Security - securing containnerized applications to prevent unauthorized access or data breaches
* API Security - protecting application programming interfaces (APIs) from unauthorized access or misuse
* 3rd-Party Vendor Management - ensuring that third-party vendors abide by security policies and standards
*Disaster Recovery - having a plan in place to recover from security breaches, system failures, or natural disasters
While implementing a completely secure system is challenging, following these simplified steps can help you design a more secure system:
- Identify assets: Determine the assets within your system that require protection, such as sensitive data, user information, or critical infrastructure. This will help you prioritize security measures.
- Perform a risk assessment: Identify potential risks and threats that could compromise the security of your system. This includes considering both internal and external threats, such as unauthorized access, data breaches, or malware attacks. Assess the impact and likelihood of each threat to prioritize your security efforts.
- Establish security requirements: Define clear security requirements based on the risk assessment. These requirements will guide the design and implementation of your secure system. Consider factors such as access controls, encryption, secure communication protocols, and incident response procedures.
- Follow the principle of least privilege: Grant users and processes only the minimum privileges necessary to perform their tasks. This reduces the potential damage that can be caused by compromised accounts or malicious insiders.
- Implement strong authentication: Use strong authentication mechanisms, such as multi-factor authentication (MFA), to verify user identities. This adds an extra layer of protection against unauthorized access.
- Apply encryption: Protect sensitive data by encrypting it both at rest and in transit. Encryption ensures that even if data is intercepted or stolen, it remains unreadable without the encryption keys.
- Implement secure coding practices: Follow secure coding guidelines and best practices to minimize the introduction of vulnerabilities. This includes input validation, output encoding, proper error handling, and regular security code reviews.
- Regularly patch and update software: Keep all software components up to date with the latest security patches and updates. This helps address known vulnerabilities and reduces the risk of exploitation.
- Implement intrusion detection and monitoring: Deploy intrusion detection systems (IDS) and security monitoring tools to detect and respond to potential security incidents. These systems can alert you to suspicious activities and help identify and mitigate threats.
- Conduct regular security assessments: Perform periodic security assessments, such as penetration testing and vulnerability scanning, to identify and address any weaknesses or vulnerabilities in your system. Regular assessments help ensure that your system remains secure over time.
- Educate users: Provide regular security awareness training to users to help them understand their role in maintaining the security of the system. Teach them about common threats, such as phishing attacks, and how to recognize and respond to them.
- Establish an incident response plan: Develop a comprehensive incident response plan that outlines the steps to be taken in the event of a security incident. This includes procedures for containment, eradication, and recovery. Regularly test and refine the plan to ensure its effectiveness.